reimplement android mkbootfs with pure java, features include: unpack: - using commons.compress - save cpio entry info on unpacking, and reload it on packing, this is called 'exact-matching' pack: using new code with the help of commons.compress - for newly added ramdisk file, its file mode falls back to 'pattern-matching' - for newly added ramdisk file that doesn't match any pattern, it will use default file mode, 'default' integration test: - enable strict cpio checking |
5 years ago | |
|---|---|---|
| aosp | 5 years ago | |
| avbImpl | 5 years ago | |
| bbootimg | 5 years ago | |
| doc | 5 years ago | |
| gradle/wrapper | 6 years ago | |
| src | 5 years ago | |
| tools | 5 years ago | |
| .gitattributes | 7 years ago | |
| .gitignore | 6 years ago | |
| .gitmodules | 7 years ago | |
| .travis.yml | 5 years ago | |
| LICENSE.md | 10 years ago | |
| README.md | 5 years ago | |
| build.gradle.kts | 5 years ago | |
| gradlew | 6 years ago | |
| gradlew.bat | 6 years ago | |
| integrationTest.py | 5 years ago | |
| settings.gradle.kts | 6 years ago | |
README.md
Android_boot_image_editor
A tool for reverse engineering Android ROM images. (working on  (Ubuntu 18.04+) and
(Ubuntu 18.04+) and  )
)
Getting Started
Installation
-
install required packages
sudo apt install device-tree-compiler lz4 xz zlib1g-dev -
get the tool
git clone https://github.com/cfig/Android_boot_image_editor.git --depth=1or clone it from mirror:
git clone https://gitee.com/cfig/Android_boot_image_editor.git --depth=1
Parsing and packing
Put your boot.img to current directory, then start gradle 'unpack' task:
cp <original_boot_image> boot.img
./gradlew unpack
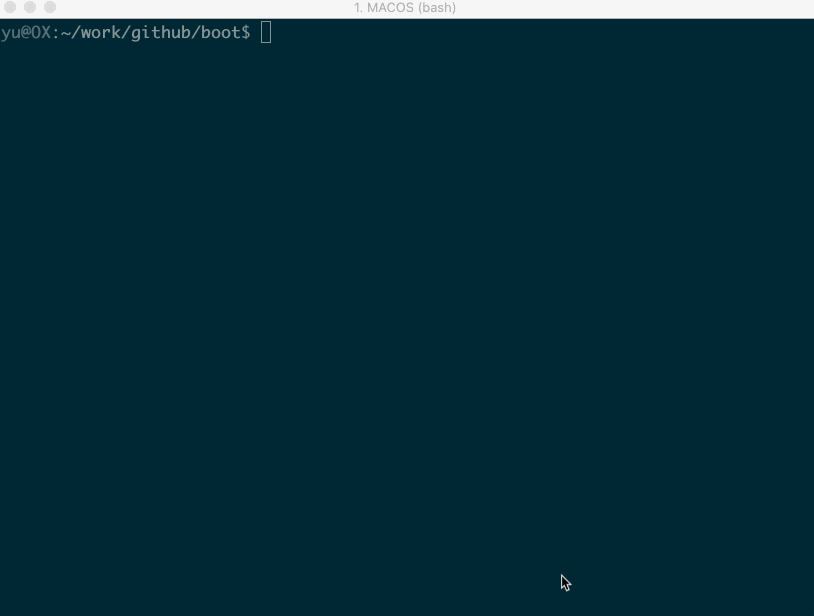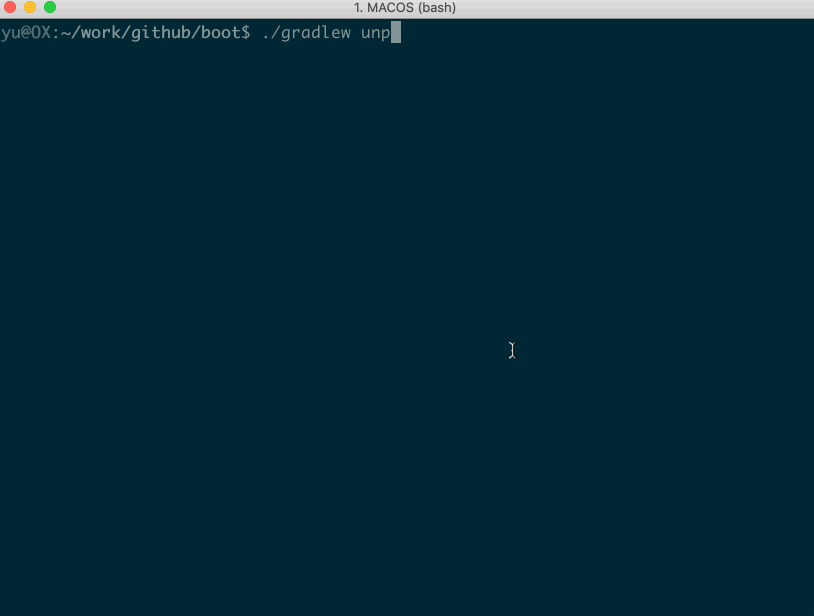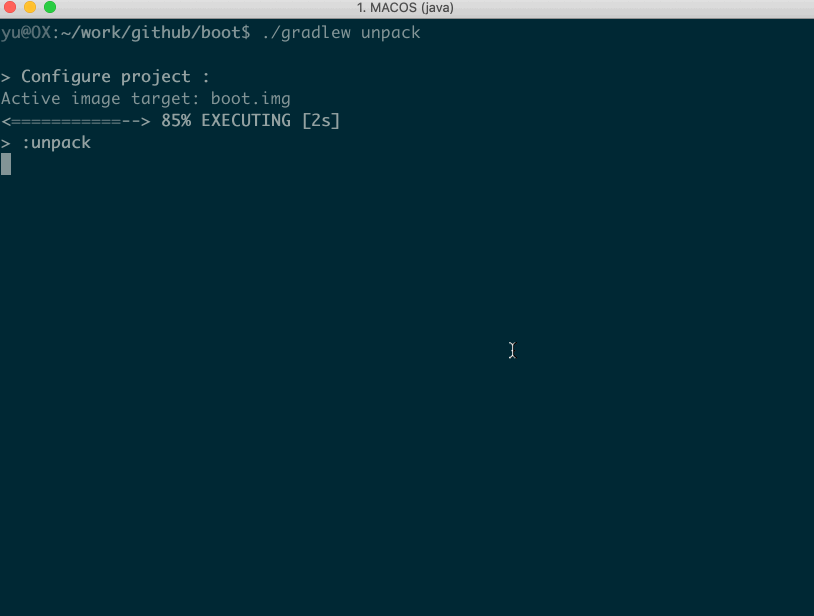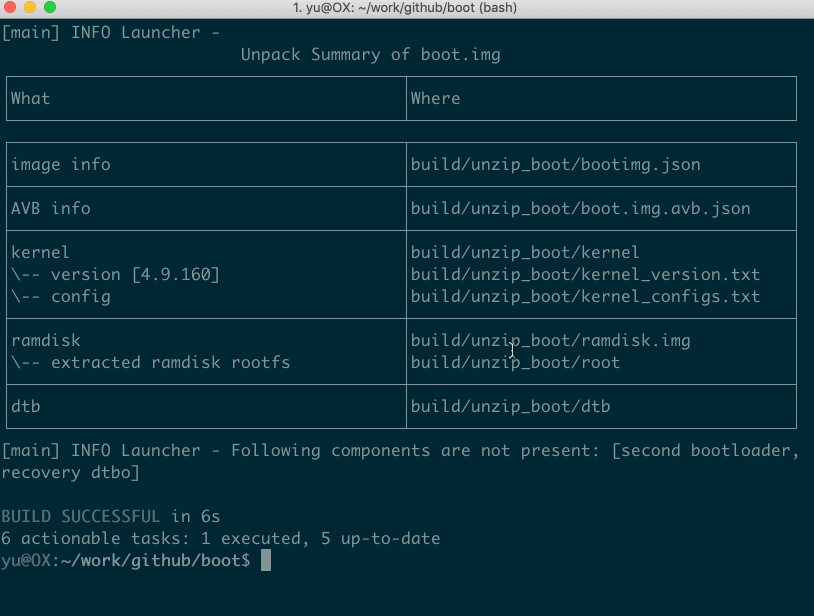
Your get the flattened kernel and /root filesystem under ./build/unzip_boot:
build/unzip_boot/
├── boot.json (boot image info)
├── boot.avb.json (AVB only)
├── kernel
├── second (2nd bootloader, if exists)
├── dtb (dtb, if exists)
├── dtbo (dtbo, if exists)
└── root (extracted initramfs)
Then you can edit the actual file contents, like rootfs or kernel. Now, pack the boot.img again
./gradlew pack
You get the repacked boot.img at $(CURDIR):
boot.img.signed
Well done you did it! The last step is to star this repo :smile
live demo
Supported ROM image types
| Image Type | file names | |
|---|---|---|
| boot images | boot.img, vendor_boot.img | |
| recovery images | recovery.img, recovery-two-step.img | |
| vbmeta images | vbmeta.img, vbmeta_system.img etc. | |
| sparse images | system.img, vendor.img etc. | |
| dtbo images | dtbo.img |
Please note that the boot.img MUST follows AOSP verified boot flow, either Boot image signature in VBoot 1.0 or AVB HASH footer (a.k.a. AVB) in VBoot 2.0.
compatible devices
| Device Model | Manufacturer | Compatible | Android Version | Note |
|---|---|---|---|---|
| Pixel 3 (blueline) | Y | 11 (RP1A.200720.009, 2020) |
more ... | |
| Pixel 3 (blueline) | Y | Q preview (qpp2.190228.023, 2019) |
more ... | |
| Pixel XL (marlin) | HTC | Y | 9.0.0 (PPR2.180905.006, Sep 2018) |
more ... |
| K3 (CPH1955) | OPPO | Y for recovery.img N for boot.img |
Pie | more |
| Z18 (NX606J) | ZTE | Y | 8.1.0 | more... |
| Nexus 9 (volantis/flounder) | HTC | Y(with some tricks) | 7.1.1 (N9F27M, Oct 2017) | tricks |
| Nexus 5x (bullhead) | LG | Y | 6.0.0_r12 (MDA89E) | |
| Moto X (2013) T-Mobile | Motorola | N | ||
| X7 (PD1602_A_3.12.8) | VIVO | N | ? | Issue 35 |
more examples
- recovery.img
If you are working with recovery.img, the steps are similar:
cp <your_recovery_image> recovery.img
./gradlew unpack
./gradlew pack
- vbmeta.img
cp <your_vbmeta_image> vbmeta.img
./gradlew unpack
./gradlew pack
- boot.img and vbmeta.img
cp <your_boot_image> boot.img
cp <your_vbmeta_image> vbmeta.img
./gradlew unpack
./gradlew pack
Your boot.img.signed and vbmeta.img.signd will be updated together.
- sparse vendor.img
cp <your_vendor_image> vendor.img
./gradlew unpack
./gradlew pack
You get vendor.img.unsparse, then you can mount it.
mkdir mnt
sudo mount -o ro vendor.img mnt
boot.img layout
Read layout of Android boot.img and vendor_boot.img.
References
boot_signer https://android.googlesource.com/platform/system/extras
cpio / fs_config https://android.googlesource.com/platform/system/core https://www.kernel.org/doc/Documentation/early-userspace/buffer-format.txt
AVB https://android.googlesource.com/platform/external/avb/
mkbootimg https://android.googlesource.com/platform/system/tools/mkbootimg/+/refs/heads/master/
Android version list https://source.android.com/source/build-numbers.html
kernel info extractor https://android.googlesource.com/platform/build/+/refs/heads/master/tools/extract_kernel.py
mkdtboimg https://android.googlesource.com/platform/system/libufdt/
libsparse https://android.googlesource.com/platform/system/core/+/refs/heads/master/libsparse/
Android Nexus/Pixle factory images https://developers.google.cn/android/images
